TryHackMe: Advent of Cyber - Day 19 - Something Phishy Is Going On
This is a write up for the Day 19 - Something Phishy Is Going On challenge in the Advent of Cyber room on TryHackMe. Some tasks may have been omitted as they do not require an answer.
Who was the email sent to? (Answer is the email address)
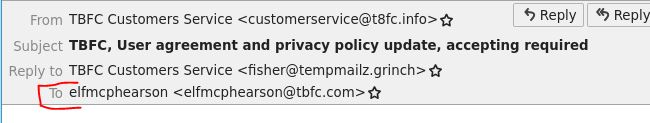
Answer: elfmcphearson@tbfc.com
Phishing emails use similar domains of their targets to increase the likelihood the recipient will be tricked into interacting with the email. Who does it say the email was from? (Answer is the email address)
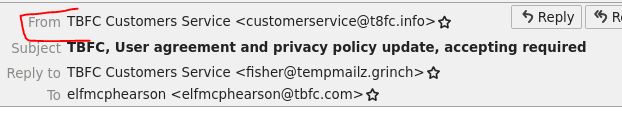
Answer: customerservice@t8fc.info
Sometimes phishing emails have a different reply-to email address. If this email was replied to, what email address will receive the email response?
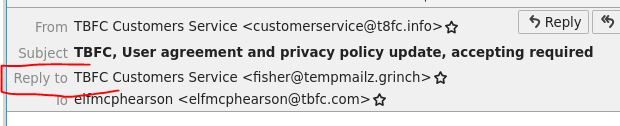
Answer: fisher@tempmailz.grinch
Less sophisticated phishing emails will have typos. What is the misspelled word?
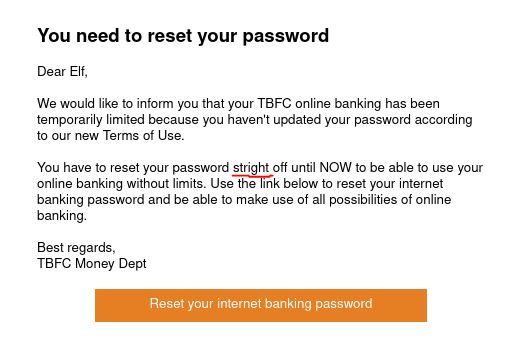
Answer: stright
The email contains a link that will redirect the recipient to a fraudulent website in an effort to collect credentials. What is the link to the credential harvesting website?
We can decode the base64 email message with CyberChef.
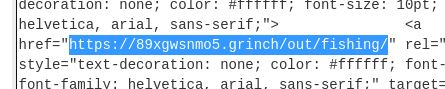
Answer: https://89xgwsnmo5.grinch/out/fishing/
View the email source code. There is an unusual email header. What is the header and its value?
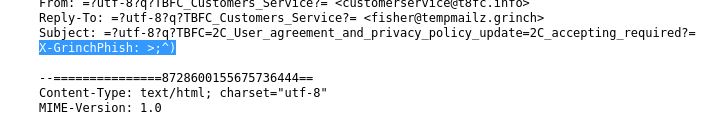
Answer: X-GrinchPhish: >;^)
You received other reports of phishing attempts from other colleagues. Some of the other emails contained attachments. Open attachment.txt. What is the name of the attachment?
head attachment.txt
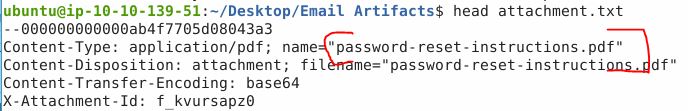
Answer: password-reset-instructions.pdf
password-reset-instructions.pdf
mcskidy@elfmode$ cat attachment-base64-only.txt | base64 -d > file.pdf will decode the output and create a PDF.
Opening the PDF reveals the flag.
Answer: THM{A0C_Thr33_Ph1sh1ng_An4lys!s}
Recap
In this task we learnt:
- About Phishing and investigating Email Headers
- Reconstructing base64 encoded artifacts