TryHackMe: Advent of Cyber - Day 23 - PowershELlF
This is a write up for the Day 23 - PowershELlF challenge in the Advent of Cyber room on TryHackMe. Some tasks may have been omitted as they do not require an answer.
What command was executed as Elf McNealy to add a new user to the machine?

Answer: Invoke-Nightmare
What user executed the PowerShell file to send the password.txt file from the administrator’s desktop to a remote server?
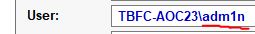
Answer: adm1n
What was the IP address of the remote server? What was the port used for the remote connection? (format: IP,Port)

Answer: 10.10.148.96,4321
What was the encryption key used to encrypt the contents of the text file sent to the remote server?
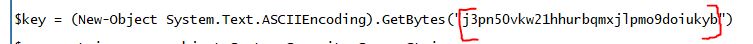
Answer: j3pn50vkw21hhurbqmxjlpmo9doiukyb
What application was used to delete the password.txt file?
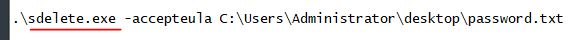
Answer: sdelete.exe
What is the date and timestamp the logs show that password.txt was deleted? (format: MM/DD/YYYY H:MM:SS PM)
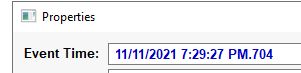
Answer: 11/11/2021 7:29:27 PM
What were the contents of the deleted password.txt file?
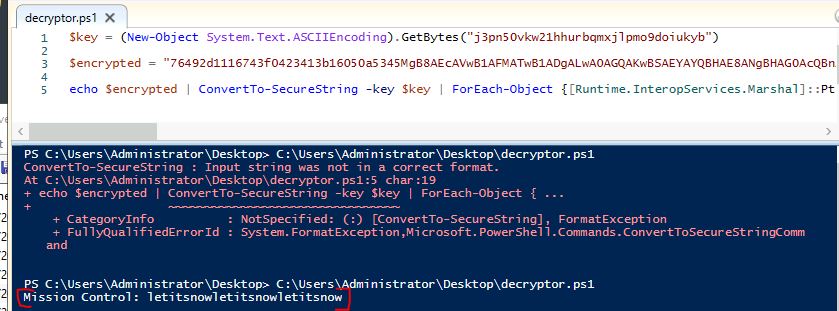
Answer: Mission Control: letitsnowletitsnowletitsnow
Recap
In this task we learnt:
- How to analyze Windows event logs to understand actions performed in an attack.
- How to recover key artifacts in unencrypted web communications.
- How to utilize PowerShell Scripting to recover a delete artifact.