TryHackMe: Nessus
This is a write up for the Scanning! and Scanning a Web Applicaiton! tasks of the Nessus room on TryHackMe. Some tasks have been omitted as they do not require an answer.
Scanning!
Create a new ‘Basic Network Scan’ targeting the deployed VM. What option can we set under ‘BASIC’ (on the left) to set a time for this scan to run? This can be very useful when network congestion is an issue.
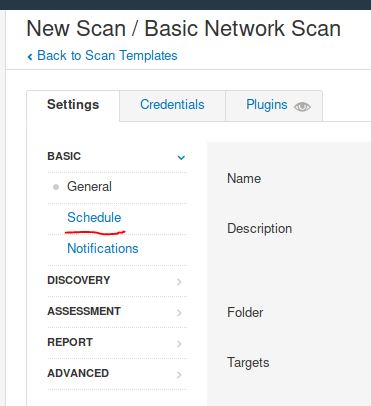
Answer: Schedule
Under ‘DISCOVERY’ (on the left) set the ‘Scan Type’ to cover ports 1-65535. What is this type called?
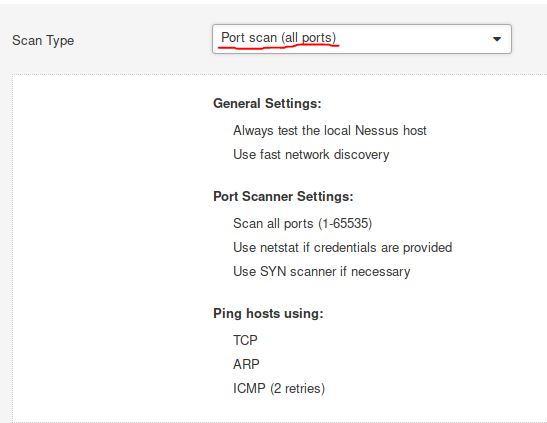
Answer: Port scan (all ports)
What ‘Scan Type’ can we change to under ‘ADVANCED’ for lower bandwidth connection?
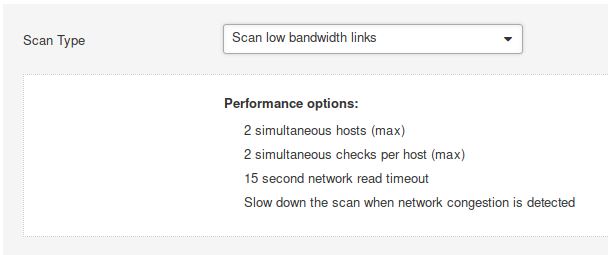
Answer: Scan low bandwidth links
After the scan completes, which ‘Vulnerability’ in the ‘Port scanners’ family can we view the details of to see the open ports on this host?
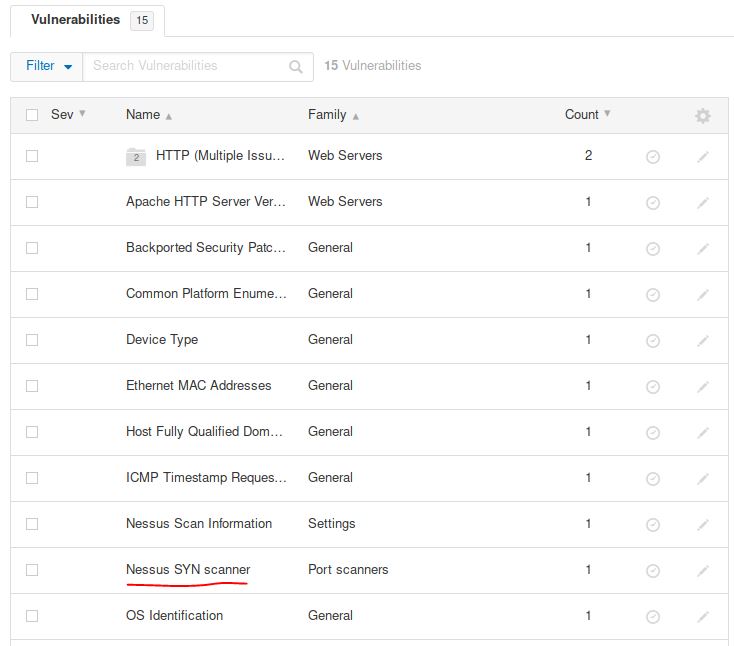
Answer: Nessus SYN scanner
What Apache HTTP Server Version is reported by Nessus?
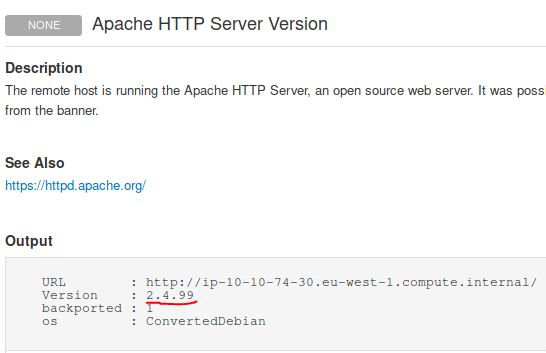
Answer: 2.4.99
Scanning a Web Application!
What is the plugin id of the plugin that determines the HTTP server type and version?
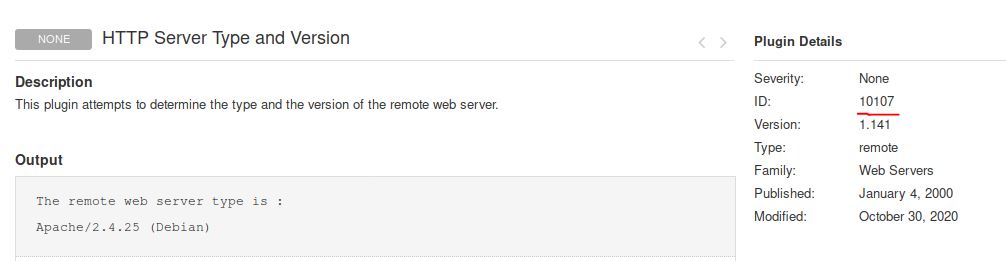
Answer: 10107
What authentication page is discovered by the scanner that transmits credentials in cleartext?
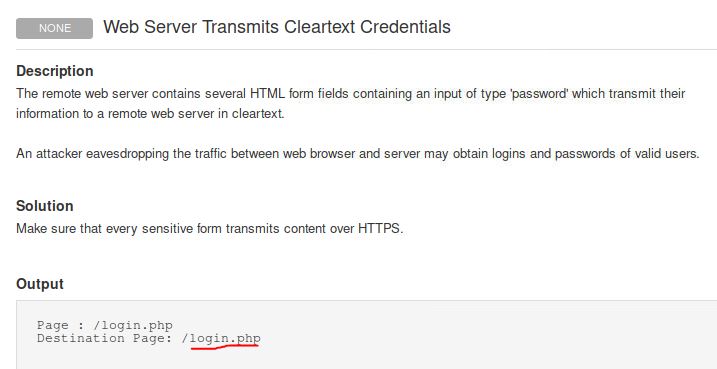
Answer: login.php
What is the file extension of the config backup?
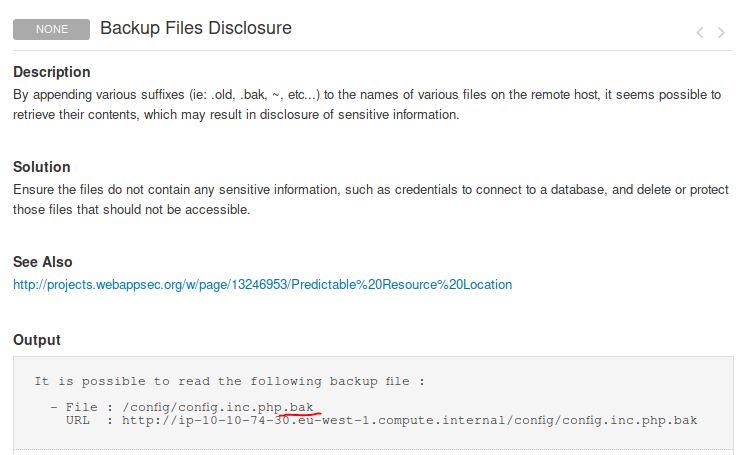
Answer: .bak
Which directory contains example documents? (This will be in a php directory)
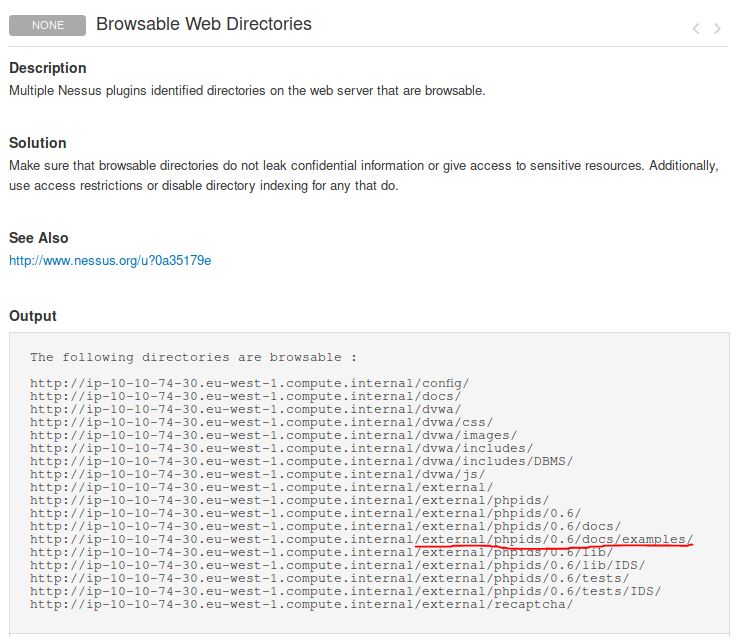
Answer: /external/phpids/0.6/docs/examples/
What vulnerability is this application susceptible to that is associated with X-Frame-Options?
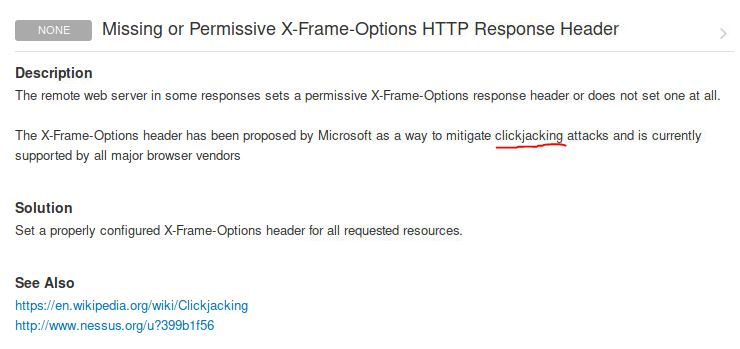
Answer: Clickjacking
Recap
In this task we learnt how to:
- Use Nessus to conduct a Basic Network Scan
- Use Nessus to conduct Web Application Tests