TryHackMe: Osquery
This is a write up for the Osquery challenge room on TryHackMe. Some tasks may have been omitted as they do not require an answer.
What is the Osquery version?
The following command will show the version information.
.version
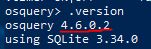
Answer: 4.6.0.2
What is the SQLite version?
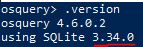
Answer: 3.34.0
What is the default output mode?
The following command will show the default output mode.
.help
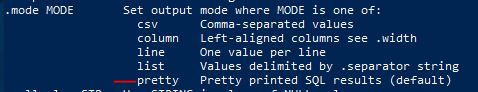
Answer: pretty
What is the meta-command to set the output to show one value per line?
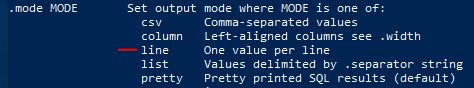
Answer: .mode line
What are the 2 meta-commands to exit osqueryi?
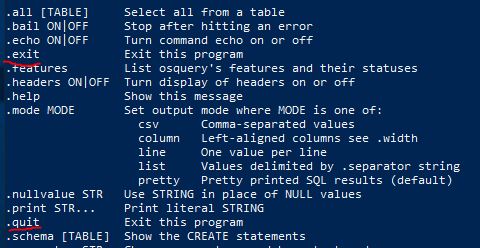
Answer: .exit, .quit
What table would you query to get the version of Osquery installed on the Windows endpoint?
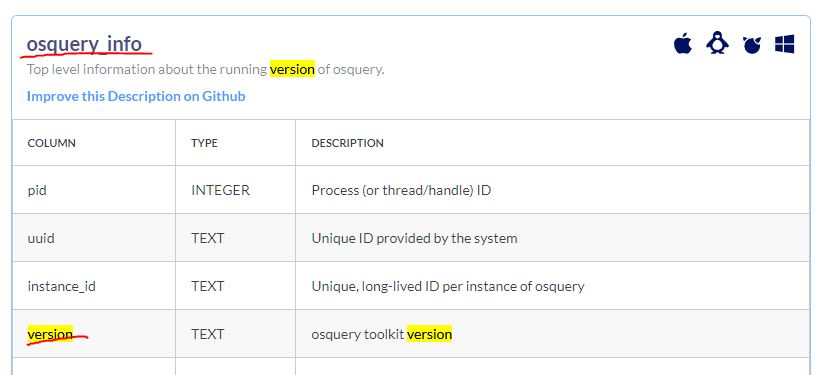
Answer: osquery_info
How many tables are there for this version of Osquery?
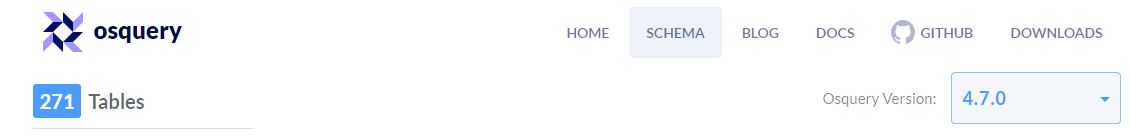
Note: The correct answer for v4.7.0 is 271 tables. However the answer set is incorrectly referring to v4.6.0 which had 266 tables. All subsequent answers will be based off v4.6.0.
Answer: 266
How many of the tables for this version are compatible with Windows?
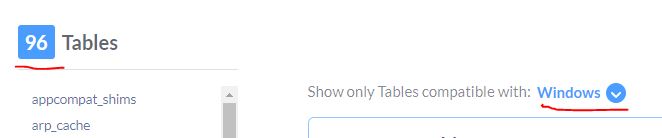
Answer: 96
How many tables are compatible with Linux?
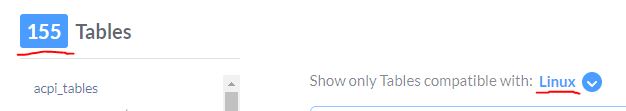
Answer: 155
What is the first table listed that is compatible with both Linux and Windows?
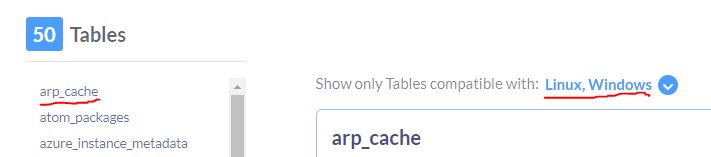
Answer: arp_cache
What is the query to show the username field from the users table where the username is 3 characters long and ends with ‘en’? (use single quotes in your answer)
Note: No results are returned as there is no username which matches the query.
Answer: SELECT username FROM users WHERE username LIKE ‘_en’
What is the Osquery Enroll Secret?
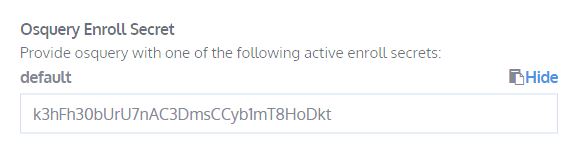
Answer: k3hFh30bUrU7nAC3DmsCCyb1mT8HoDkt
What is the Osquery version?
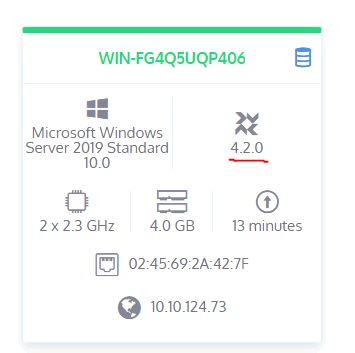
Answer: 4.2.0
What is the path for the running osqueryd.exe process?
Answer: C:\Users\Administrator\Desktop\launcher\windows\osqueryd.exe
According to the polylogyx readme, how many ‘features’ does the plug-in add to the Osquery core?
This answer is out of date, it should be 25 features.
Answer: 23
What is the ‘current_value’ for kernel.osrelease?
SELECT * FROM kernel_info
Answer: 4.4.0-17763-Microsoft
What is the uid for the bravo user?
SELECT * FROM username LIKE "%bravo%"
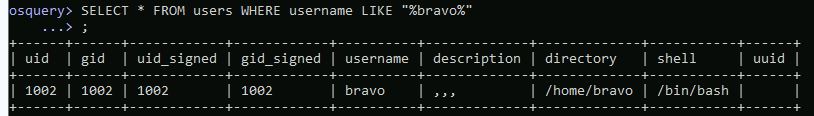
Answer: 1002
One of the users performed a ‘Binary Padding’ attack. What was the target file in the attack?
SELECT * FROM shell_history
This command reveals a file called ‘notsus’, which is definitely sus.
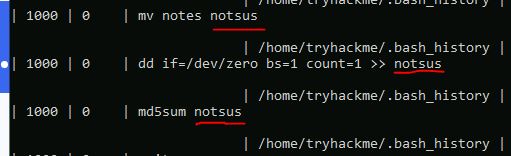
Answer: notsus
What is the hash value for this file?
md5sum notsus
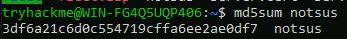
Answer: 3df6a21c6d0c554719cffa6ee2ae0df7
Check all file hashes in the home directory for each user. One file will not show any hashes. Which file is that?
The answer is fleet.zip, but the command md5sum fleet.zip still returns a hash.
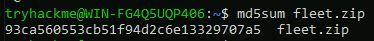
Answer: fleet.zip
There is a file that is categorized as malicious in one of the home directories. Query the Yara table to find this file. Use the sigfile which is saved in ‘/var/osquery/yara/scanner.yara’. Which file is it?
SELECT * FROM yara WHERE path = "/home/charlie/notes" AND sigfile = "/var/osquery/yara/scanner.yara";
Answer: notes
What were the ‘matches’?
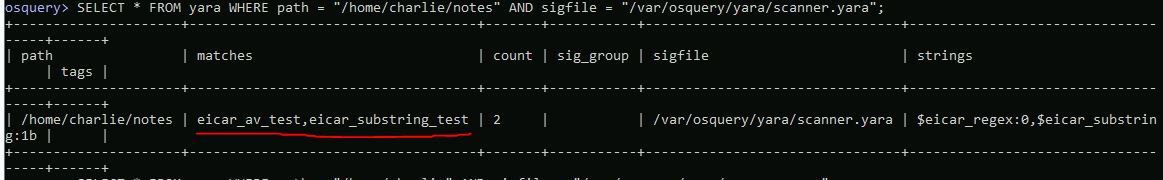
Answer: eicar_av_test,eicar_substring_test
Scan the file from Q#3 with the same Yara file. What is the entry for ‘strings’?
SELECT * FROM yara WHERE path = "/home/tryhackme/notsus" AND sigfile = "/var/osquery/yara/scanner.yara";
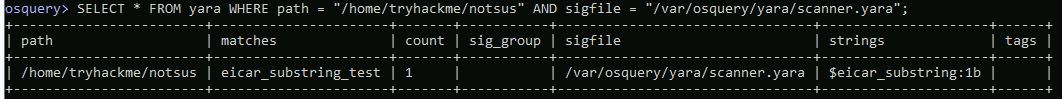
Answer: $eicar_substring:1b
What is the description for the Windows Defender Service?
SELECT * FROM services WHERE name LIKE "%WinD%";
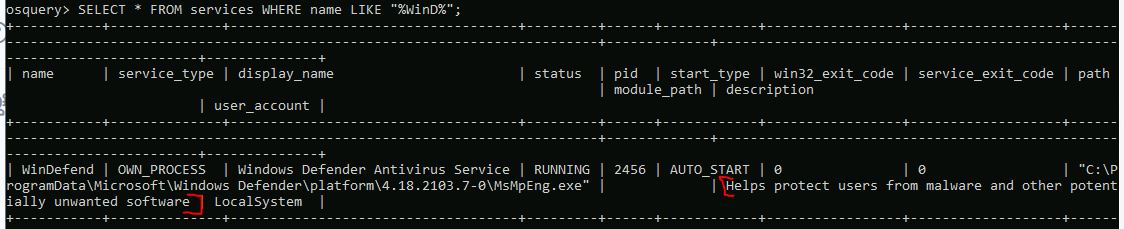
Answer: Helps protect users from malware and other potentially unwanted software
There is another security agent on the Windows endpoint. What is the name of this agent?
SELECT name FROM programs;
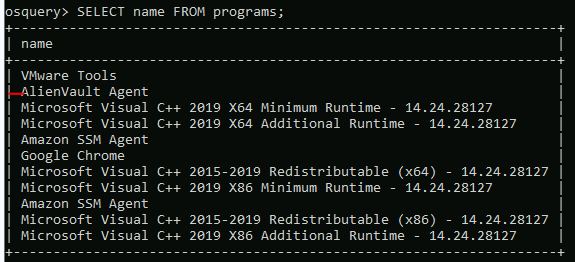
Answer: AlienVault Agent
What is required with win_event_log_data?
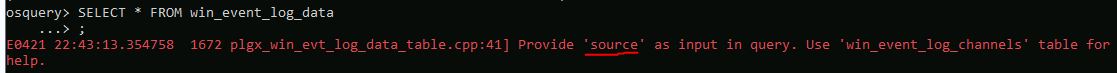
Answer: source
How many sources are returned for win_event_log_channels?
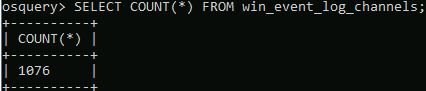
Answer: 1076
What is the schema for win_event_log_data?
.schema win_event_log_data
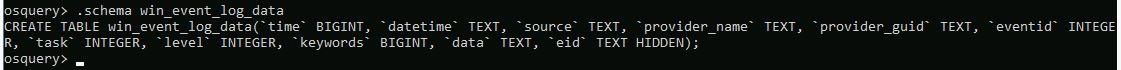
Answer: CREATE TABLE win_event_log_data(
timeBIGINT,datetimeTEXT,sourceTEXT,provider_nameTEXT,provider_guidTEXT,eventidINTEGER,taskINTEGER,levelINTEGER,keywordsBIGINT,dataTEXT,eidTEXT HIDDEN);
The previous file scanned on the Linux endpoint with Yara is on the Windows endpoint. What date/time was this file first detected? (Answer format: YYYY-MM-DD HH:MM:SS)
Answer: 2021-04-01 00:50:44
What is the query to find the first Sysmon event? Select only the event id, order by date/time, and limit the output to only 1 entry.
Answer: SELECT eventid FROM win_event_log_data WHERE source=”Microsoft-Windows-Sysmon/Operational” ORDER BY datetime LIMIT 1;
What is the Sysmon event id?
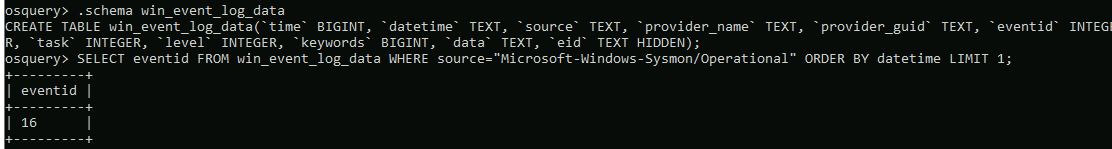
Answer: 16
Recap
In this task we learnt:
- The purpose of Osquery and basic functionality
- Querying the results of yara scans